Creating a wifi hotspot from your system(PC/Laptop) is a cool trick that we can use to perform numerous activities depending upon the user. This trick can be used by both an attacker/hacker as well as normal people. Attacker can use it to create open networks. As we already know that open networks are dangerous and are not secured at all. Open network leaves traffic unencrypted and even attack such as man-in-the-middle based attackes are widely famous in open networks. This is one of the huge trust issue with open networks hence it is always suggested not to connect to an open network such as public wifi. Similarly, normal people with good intention can also use it to create a hotspot of the connected network on which several other people can connect. It is a very simple and easy trick that can be done in couple of minutes.
Step 1:- Open Command Prompt
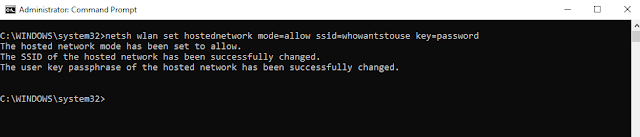
Step2:- Type:- netsh wlan set hostednetwork mode=allow ssid=Nameofthehotspot key=password
In case of above example we created a hotspot by the name of 'whowantstouse' and have set the password/key as password.
Step3:- Type:- netsh wlan start hostednetwork
Step4:- Check if the network/hotspot is visible to anyother device or not.
As we can see that the cell phone is showing the network/hotspot 'whowantstouse'
Step5:- After the hopspot is visible try connecting to the network using the password or else just connect to it if its an open network(if key is not set).
There is an error that popped up because the device says that internet is not available in the network/Hotspot.
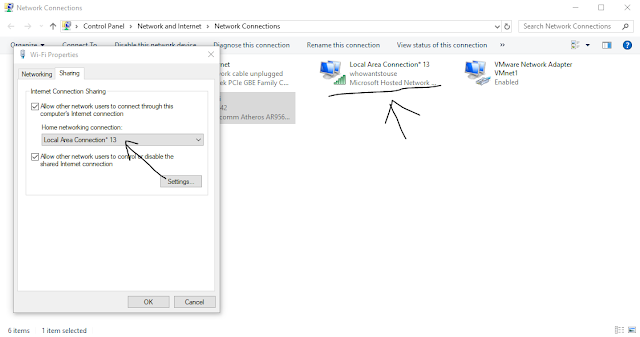
Step6:- The hotspot might not work cause we have to do some changes to our original network properties. In order to do that type 'ncpa.pcl' in run(win+r) or can directly go to ControlPannel-> Network and Internet-> Network Connections.
Once redirected to the particular place left click in the original network and click on properties.
Once clicked on properties go to the shared tab and tick mark on the allow other network option and select the hopspot network from the dropdown list.
Step7:- Try connecting again through another device and it will work smoothly.
If you have any query regarding this please leave a comment down in the comment section.









Comments
Post a Comment